RSS feeds have been around for decades, once very popular with geeks as a lightweight way of keeping up with the news such as https://feeds.bbci.co.uk/news/rss.xml before we all got 1gb cable connections and 5g, not normally read raw by human …
Category Archives: DDos
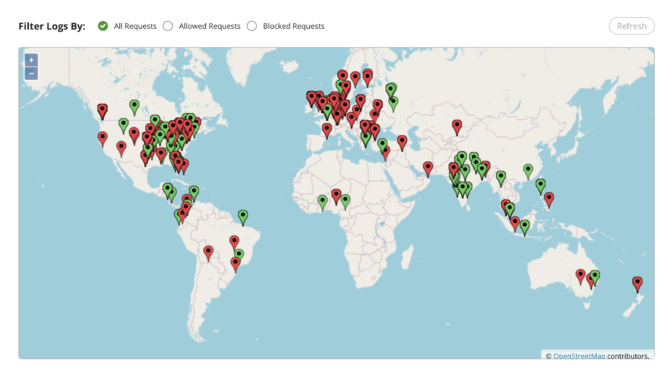
WAFs -v- Endpoint Plugins
I’ve been reading some misleading articles on the subject of Endpoint vs Cloud Security, most notably this from Wordfence . Ironically I have used Wordfence a lot, their free plugin is often my first choice as a recommendation for someone …
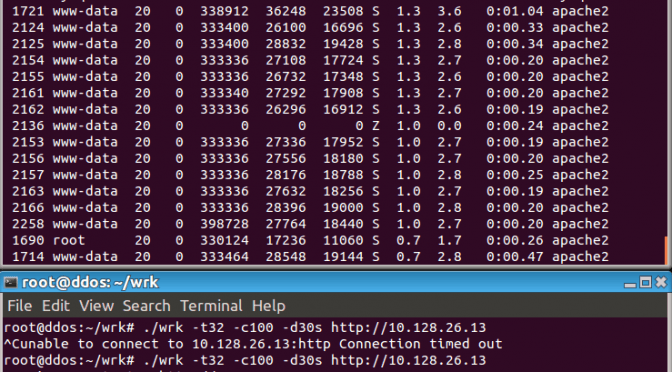
DDoS on WordPress using the search feature
This fairly low tech DDoS can easily take down an under resourced WordPress website, what you will see in your logs is something like:
| /?s=SwCGbtyTPFbgIy | 19:02:40 |
| /?s=rNiwiuFckGegR | 19:02:49 |
| /?s=SwCGbtyTPFbgIy | 19:02:53 |
| /?s=SwCGbtyTPFbgIy | 19:02:56 |
| /?s=SwCGbtyTPFbgIy | 19:03:01 |
| /?s=mYwyTaXVqvlW | 19:03:12 |
| /?s=SwCGbtyTPFbgIy | 19:03:18 |
| /?s=mYwyTaXVqvlW | 19:03:22 |
Cyberwar on free speech and small businesses
 The last month has seen an major increase in international cyber warfare, first we had North Korea hacking Sony, apart from the embarrassment caused by leaked documents, forced them to shut down their entire network, and they claim still some …
The last month has seen an major increase in international cyber warfare, first we had North Korea hacking Sony, apart from the embarrassment caused by leaked documents, forced them to shut down their entire network, and they claim still some …