I’ve been reading some misleading articles on the subject of Endpoint vs Cloud Security, most notably this from Wordfence . Ironically I have used Wordfence a lot, their free plugin is often my first choice as a recommendation for someone …
Category Archives: WordPress
Switching a WordPress site over to HTTPS/SSL
WordPress.com, the official hosted version of WordPress have switched over to enforcing SSL, while this is mostly a political statement, there is some merit, firstly you might actually have some forms which should be secure, allowing users to …
Adding disclaimers on blog comments
I was asked a couple of days ago to add a disclaimer to the commenting section on a WordPress Blog, something like: “Commentators are asked to be polite, stay on topic. While we do monitor and moderate comments, they are …
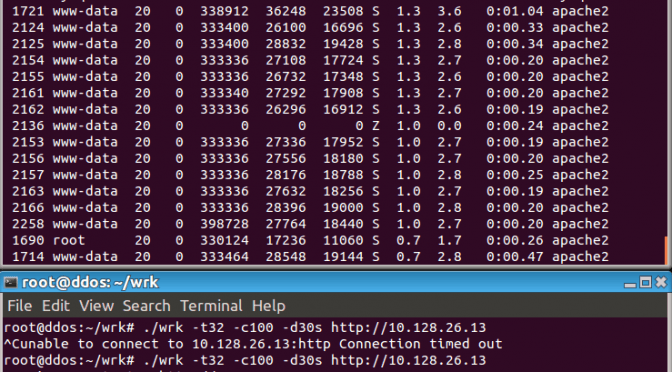
Dealing with DDoS attacks against WordPress sites and blogs
Blog Spammers and which CAPTCHA, 5 reviewed
CAPTCHA, standing for “Completely Automated Public Turing test to tell Computers and Humans Apart” has been around since 2000, so was already fairly well developed when the bots started targeting blogs, guest books and wiki’s which are the main target …
Migrating a large Blog installation from Movable Type to WordPress, lessons learned
First, although Movable Type is rock solid, personally I like it a lot but a number of apparently unsurpassable issues have come up that negatively affect the client, the once vibrant open source community that supported MT is now gone …