Small businesses with Exchange Server or other mail servers tend to have their mail server physically located in their office (in a DMZ), which is great for performance and communicating with each other, but they tend to run all their …
Category Archives: Spam
AntiCrawler, referrer spam turned nasty
AntiCrawler, referrer spam turned nasty, asking you to add potentially malicious code to your own site.
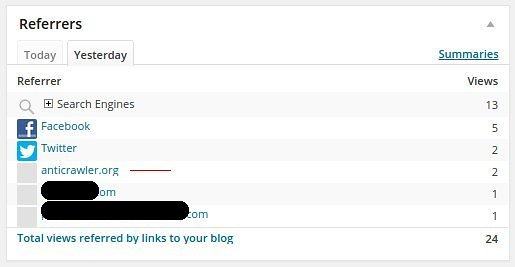 Although this is by far not the most popular blog, I do like to look in each day to check up on things, and …
Although this is by far not the most popular blog, I do like to look in each day to check up on things, and …
Fake domain name sales
I was so happy with the response I got with my post regarding the fake ICANN appraiser scam a couple of months ago, I thought it worth sharing each of the dodgy domain name practices I come across as they …
Blog Spammers and which CAPTCHA, 5 reviewed
CAPTCHA, standing for “Completely Automated Public Turing test to tell Computers and Humans Apart” has been around since 2000, so was already fairly well developed when the bots started targeting blogs, guest books and wiki’s which are the main target …
A large scam of a type I’ve not seen before
A client contacted me unsure whether the be honored or worried when he came across his own site completely cached on another domain name “domainname.newvirtuallife.com”, doing a Google of the domain name “newvirtuallife.com” gave me dozens of other examples of …
Spammers, its nothing personal
Over the last week I’ve been helping out a couple of bloggers on WordPress issues.
Both have similar problems, despite having captchas enabled on registration. Both have ridiculous numbers of fake subscribers (one, 5000+ a week), an equally high number …