Small businesses with Exchange Server or other mail servers tend to have their mail server physically located in their office (in a DMZ), which is great for performance and communicating with each other, but they tend to run all their anti-spam and virus filtering on the same server. This brings up a number of issues.
- Windows Server anti virus and anti spam products tend to be resource intensive.
- Legislation in most locals require that all email is archived for x number of years, if you receive 80% spam on your email, it means that to.
- Your DNS MX record is being advertised to the world, while security through obscurity is never the answer, why advertise your public IP.
- RBLs will blacklist your public IP if you are found to have a spam producing virus, causing your outbound mail to bounce, it can take weeks to get off GMail and Hotmail’s spam lists.
- Some ISPs are not reliable, while a small office maybe unhappy about not having internet access for half a day, missing emails can have a greater business impact.
- It’s rare, but some ISPs will block port 25 which is used to relay mail between servers if they see what they consider as abuse, normally sending a warning first.
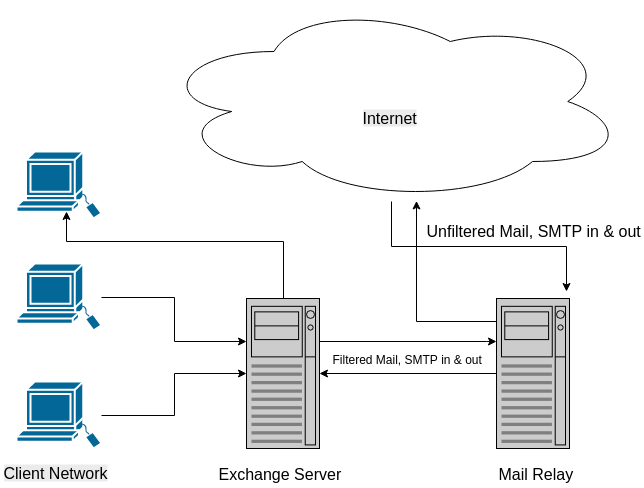
The answer to these risks is hosting a mail relay off-site, maybe even 2 if you want that resilience, but over the last 5 years, apart from reboots forced by updates taking 10 minutes every few months, I’ve not seen a customer impacting outage.
Your office mail server can block all incoming and outgoing SMTP traffic except between the mail relay, deleting the most obvious spam and all the viruses before the mail is delivered to your office. Also filtering outgoing email, ensuring you are not spreading viruses in the company’s name, and enforcing any other security policies you may have in place. Most abuse against an Exchange Server is against port 25, the public will not even see it exists. It will make it far less obvious what your public IP is.
You can block on your firewall all smtp traffic on the network except between the Server and the Relay, if someone brings in a an infected laptop and joins your network, it wont get you RBL listed, and the ISP wont block your port 25.
I have for more than a decade used Symantec Endpoint Protection for this purpose, but their SMTP relay can only be installed on bare metal or in a virtual machine, also for some strange reason require separate IP addresses for inbound and outbound and the costs are not so low for these to be hosted outside the office, and the performance and usability is no better than a free mail relay package such as MailScanner, which can easily be installed on a small cloud instance, as a guide I have 50 (heavy) users using one $20 a month DigitalOcean instance, and the processor and memory never goes over 20% and 600 (more regular) users using 2x $40 instances at different data centers.
This mitigation in no way suggests that you do not run anti-virus software on the workstations, this is still essential as not all virus infection come from email, and you should still have anti-spam filtering to fine tune the removal of the less obvious spam as it is simplest to set the relay to only delete the obvious, Microsoft own filter is usually ample for this.
While MailScanner itself is free, some of the RBL and signature subscriptions can be pricey, but a default installation which include amongst others Clam AV. Spam detection and Spamassassin is fine in most cases, also unlike Symantec’s pricing model, most additions to MailScanner are not charged at a per user license model.
This model works just as well in a distributed environment if you have a co-located mail server. Even adding a mail relay to a heavily firewalled website that wanted to hide the real IP of the host which was previously being leaked in automated emails from the site leading to a level 3/4 DDoS attack.
If you want assistance in setting such a configuration up, I am always available for hire, and if you have a suggestion to improve on this model, I am always willing to learn.