(TLDR solution is to allowlist the Twitter API IP address ranges)
Around 3 weeks back, the end of May I had reports of WordPress authors unable to embed tweets in posts, some using classic editor, others block editor.
The …

(TLDR solution is to allowlist the Twitter API IP address ranges)
Around 3 weeks back, the end of May I had reports of WordPress authors unable to embed tweets in posts, some using classic editor, others block editor.
The …
Online threats to consumers come in many forms, such as viruses, malware, phishing scams, and ransomware. These threats can compromise the security of a person’s personal information, such as their login credentials and credit card numbers, and can lead to …
Как обойти блокировку BBC в России
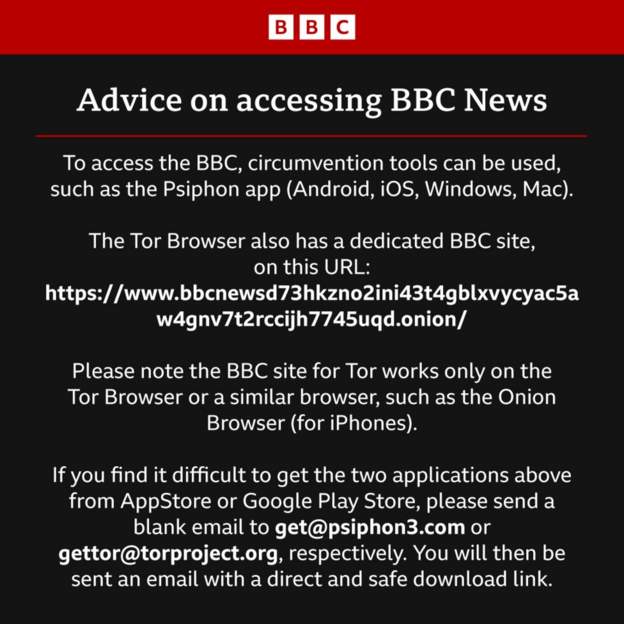
Sharing this as obviously the link that the Beeb shared here can not be seen if forwarded to a Russian, as of course, Russia has blocked all disenting voices, and as this is …
I’m pretty confused as to why there is so little written in the mainstream news on the scale and implications of this latest, and by far the largest, one of many attacks on our network infrastructure, and by a state …
I have some great security headers on this blog, but they are added using a single checkbox on the Sucuri WAF (web application firewall) this site uses. This is what they look like:
x-xss-protection: 1; mode=block x-frame-options: SAMEORIGIN x-content-type-options: nosniff…
There was a recent arrest of a 19 year old in Halifax for “hacking” freedom-of-information releases from a government website. Alleging he is guilty of section 342.1 of the criminal code, which prohibits unauthorized uses of computers “with intent to …
Everytime governments try to break encryption on social media, and they are doing it a lot these days, they hold up an example such as in this case “Sex Traffickers” so if you dare question them, you are exposed as …
There is a mostly unreported and unrecognised ongoing attack on our research institutes, commerce and infrastructure, massively damaging our successes in the western world.
UC Cert, the United States Computer Emergency Team released an update (TA17-117A) last week from the …
I’ve been reading some misleading articles on the subject of Endpoint vs Cloud Security, most notably this from Wordfence . Ironically I have used Wordfence a lot, their free plugin is often my first choice as a recommendation for someone …
Small businesses with Exchange Server or other mail servers tend to have their mail server physically located in their office (in a DMZ), which is great for performance and communicating with each other, but they tend to run all their …