Well not quite hacking as most people think of it, but technically it is, and it’s great.
There is a common theme when you have cleared up some malware for someone, likely they have spent a while confused by what’s …
Well not quite hacking as most people think of it, but technically it is, and it’s great.
There is a common theme when you have cleared up some malware for someone, likely they have spent a while confused by what’s …
WordPress.com, the official hosted version of WordPress have switched over to enforcing SSL, while this is mostly a political statement, there is some merit, firstly you might actually have some forms which should be secure, allowing users to …
From Microsoft’s warning is not clear what the vulnerability is, but you can see that this is critical, and the vulnerability must be patched, especially on public facing Windows IIS Servers:
…A remote code execution vulnerability exists in the HTTP
VPN offer far more security than the proxy servers which most people are used to using, when using commercial paid for services proxy server accounts are normally much cheaper and simpler to set-up for the client which is their only …
AntiCrawler, referrer spam turned nasty, asking you to add potentially malicious code to your own site.
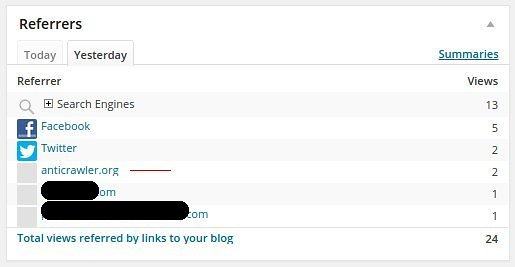 Although this is by far not the most popular blog, I do like to look in each day to check up on things, and …
Although this is by far not the most popular blog, I do like to look in each day to check up on things, and …
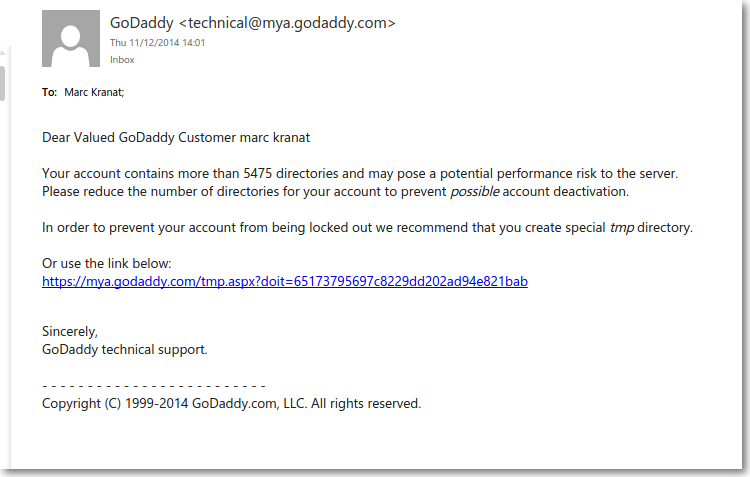 I do get a lot of phishing emails, we all do, but as security professionals we tend to recognise them immediately, the syntax is wrong, it’s missing a name, of course when you get them from a bank you don’t …
I do get a lot of phishing emails, we all do, but as security professionals we tend to recognise them immediately, the syntax is wrong, it’s missing a name, of course when you get them from a bank you don’t …
 Most browsers are vulnerable, there were plans a remove SSL3 anyway. Here’s a simple test and supplied fixes for most browser types on most platforms.
Most browsers are vulnerable, there were plans a remove SSL3 anyway. Here’s a simple test and supplied fixes for most browser types on most platforms.
General details on the Poodle SSL3 vulnerability here.
A fix for Poodle SSL3 Microsoft …
People are still busy going through previous projects and installations the growing number of threats offered by the Shell Shock vulnerability, with the list of exploits are constantly growing here.
Well I didn’t quite drop everything, but within 24 …
JPMorgan Password Leads Hackers to 76 Million Households
Inexcusable that there was only a password protecting this much sensitive data.
2FA, Smart Card… we have so many tools available now, there really is no excuse for such …