I’ve seen various figures on the recent increase in DDoS (Distributed Denial of Service) attacks from various sources, if you use the figures from this story in PCmag, which might me more of an advert for Arbor using just quantity of raw bandwidth, it has doubled in 6 months. I know that a number of my clients have seen far more the last few months, with one WordPress blog seeing spikes of 40,000 requests a second, where as last year it saw far less than half that, its easily handled though with 4 load balanced firewalls, but this is an entirely different story than what a small blog like this sees.
What I see on average sites and blogs built on WordPress, I say average as the vast majority of websites on the internet are made up of small points of presence for small businesses and opinionated people like me getting their thoughts out there, and WordPress is by far the most popular platform. We’ve also become a target, and for most of us the DDoS is not intentional, it’s the vast number of bots, both computers that have a trojan acting as a zombie and other compromised websites that are trying to recruit your website into their army, and maybe also steal your user list. Of course you might have also attracted some unwelcome attention from a competitor and the DDoS is intentional.
you only need look at an attack map such as Norse to see what sort of attacks are going on right now, normally HTTP attacks are listed at number 2 after SSH, attacks at HTTP, port 80 mean attacks at the actual website. And they are mostly hitting the hosting companies of small websites such as mine, GoDaddy.
The most popular targets in this order are:
- /wp-login.php
- /wp-login.php?action=register
- /wp-comments-post.php
Attacks against “/wp-login.php” are password guessing, while they seem to be totally dim at guessing the password to “admin” an account that doesn’t even exist, when you get hit by a few thousand in a short period of time, it can take you off line, causing you to run out of resources, while they might only be interested in hacking your server, they cause a DDoS. This is potentially by far the worst of the attacks, as they often infect the site with malware to infect the sites browsers, This can mostly be easily mitigated by just changing the login path from “/wp-login.php” to something else, and making sure the user “admin” does not exist. abusers rarely check what they are attacking, simply checking the name of the sites owner, or what url you actually login at, and this can be changed manually or simply using a plugin such as Rename wp-login, which also helps with the next issue.
Attempts to register at “/wp-login.php?action=register”, are the spammers trying to create accounts to leave spam on your posts. This can be very frustrating when you find 99.9% of your users are fake accounts, and I have seen relatively quiet blogs run at a snails pace when they notice and try to manage the 100,000 users they have accumulated over a number of years. This is quite ironic as I have seen this on business sites that don’t allow commenting, and have no reason for users to have accounts, and the reverse is true here, currently on this site I don’t require accounts to comment, which brings me to my third on the list.
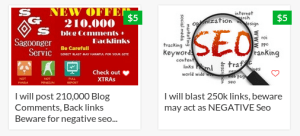 Spam attacks against “/wp-comments-post.php”, while there is a market for “SEO Links”, this will continue, checking on the latest prices, the spammers are now offering quarter of a million spam “comments” on websites and blogs for $5 on fiverr.com, they do these even warning you that such back-links will negatively effect your SEO (strange eh?). Again, this will burden a small site, slowing it down, and I have seen A way to control this that works (for now) is adding a captcha as I have done.
Spam attacks against “/wp-comments-post.php”, while there is a market for “SEO Links”, this will continue, checking on the latest prices, the spammers are now offering quarter of a million spam “comments” on websites and blogs for $5 on fiverr.com, they do these even warning you that such back-links will negatively effect your SEO (strange eh?). Again, this will burden a small site, slowing it down, and I have seen A way to control this that works (for now) is adding a captcha as I have done.
There is another recently used vulnerability, “WordPress XML-RPC PingBack Vulnerability“, it’s existed for 7 years, but someone only just got around to deploying it, there is not much you can do if you are the target, but it’s fairly easy to block ping-backs so you don’t become one of the unsuspecting attackers. Because of the nature of this DDoS attack, using legitimate methods, it’s probably not even included in the attack map numbers above.
And then there is a whole list of other threats, not so easily listed as there are so many variants, exploits looking to take advantage of vulnerabilities in plugins, to avoid these issues, you can just don’t use plugins or when you do, only use well maintained and regularly updated plugins. But these are not DDoS attacks, quite the opposite, once they have compromised a site, they want it to be available so they can push their spam and compromise as many others as it can.
More and more sites are suffering, and these are only a few attack vectors that those trying to make a living selling back-links or those with far more malicious intent are looking to take advantage of.
It’s becoming far too many threats for most website owners to worry about, it’s easy for me, I’ve been doing this for years, while it doesn’t solve all security threats there is another option that works well, well I would say this as I do a lot of work for Sucuri as a firewall analyst :), and that is putting your site or blog behind a cloud hosted firewall such as CloudProxy, which filters all traffic and takes any beating for you.
2 thoughts on “Dealing with DDoS attacks against WordPress sites and blogs”