I’ve been reading some misleading articles on the subject of Endpoint vs Cloud Security, most notably this from Wordfence . Ironically I have used Wordfence a lot, their free plugin is often my first choice as a recommendation for someone …
All posts by Marc Kranat
Reinventing the Web
We’ve seen some successful technical “reinventions” of the Web such as HTTPS/2 and HTML5 making sites faster and more responsive, but this “Web’s Creator Looks to Reinvent It” initiative is not new, but I will come to that later.
There …
Enabling HSTS
HTTP Strict Transport Security is a very simple to deploy addition to HTTPS, it doesn’t enforce SSL itself but it uses pre-populated lists such as Google’s here. Allowing clients browsers to check against, simply that the site only delivers …
Using an SMTP mail relay to secure a network
Small businesses with Exchange Server or other mail servers tend to have their mail server physically located in their office (in a DMZ), which is great for performance and communicating with each other, but they tend to run all their …
Hacking the Hackers
Well not quite hacking as most people think of it, but technically it is, and it’s great.
There is a common theme when you have cleared up some malware for someone, likely they have spent a while confused by what’s …
Switching a WordPress site over to HTTPS/SSL
WordPress.com, the official hosted version of WordPress have switched over to enforcing SSL, while this is mostly a political statement, there is some merit, firstly you might actually have some forms which should be secure, allowing users to …
Local man tricks upto 2000 boys into exposing themselves online
I don’t think kids are getting the message, allowing anything that you would not be comfortable for your mother to see, should never be allowed onto any digital device, from explicit text messages to embarrassing pictures, never, I don’t know …
Critical Vulnerability in Windows IIS – HTTP.sys PoC (MS15-034)
From Microsoft’s warning is not clear what the vulnerability is, but you can see that this is critical, and the vulnerability must be patched, especially on public facing Windows IIS Servers:
…A remote code execution vulnerability exists in the HTTP
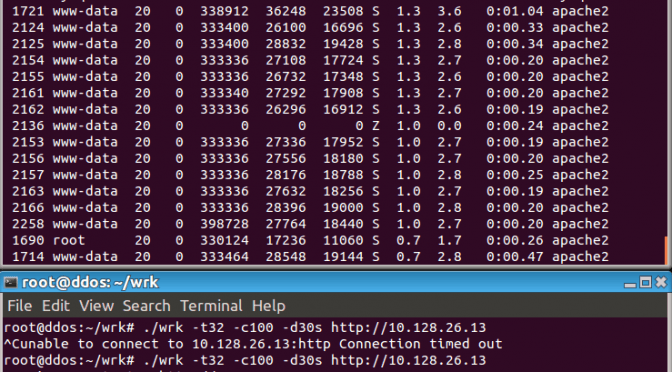
DDoS on WordPress using the search feature
This fairly low tech DDoS can easily take down an under resourced WordPress website, what you will see in your logs is something like:
| /?s=SwCGbtyTPFbgIy | 19:02:40 |
| /?s=rNiwiuFckGegR | 19:02:49 |
| /?s=SwCGbtyTPFbgIy | 19:02:53 |
| /?s=SwCGbtyTPFbgIy | 19:02:56 |
| /?s=SwCGbtyTPFbgIy | 19:03:01 |
| /?s=mYwyTaXVqvlW | 19:03:12 |
| /?s=SwCGbtyTPFbgIy | 19:03:18 |
| /?s=mYwyTaXVqvlW | 19:03:22 |
Setting up a Simple VPN Server
VPN offer far more security than the proxy servers which most people are used to using, when using commercial paid for services proxy server accounts are normally much cheaper and simpler to set-up for the client which is their only …