The last month has seen an major increase in international cyber warfare, first we had North Korea hacking Sony, apart from the embarrassment caused by leaked documents, forced them to shut down their entire network, and they claim still some …
The last month has seen an major increase in international cyber warfare, first we had North Korea hacking Sony, apart from the embarrassment caused by leaked documents, forced them to shut down their entire network, and they claim still some …
All posts by Marc Kranat
AntiCrawler, referrer spam turned nasty
AntiCrawler, referrer spam turned nasty, asking you to add potentially malicious code to your own site.
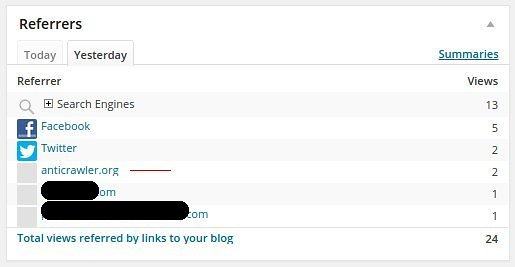 Although this is by far not the most popular blog, I do like to look in each day to check up on things, and …
Although this is by far not the most popular blog, I do like to look in each day to check up on things, and …
Fake GoDaddy DNS Notifications
Only last week I posted about another phishing scam targeting GoDaddy clients, this client only just bought his first domain last week. He knew nothing should have been changed, so luckily when he got the email notification “Status Alert: Domain …
Highly targeted Phishing against a GoDaddy account
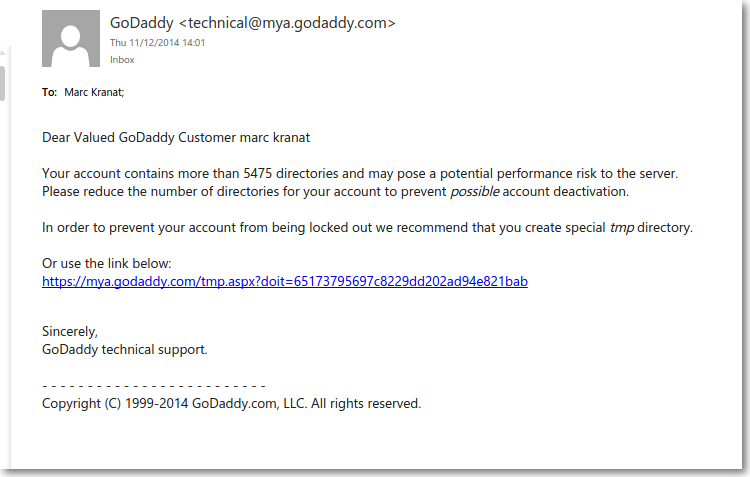 I do get a lot of phishing emails, we all do, but as security professionals we tend to recognise them immediately, the syntax is wrong, it’s missing a name, of course when you get them from a bank you don’t …
I do get a lot of phishing emails, we all do, but as security professionals we tend to recognise them immediately, the syntax is wrong, it’s missing a name, of course when you get them from a bank you don’t …
Adding disclaimers on blog comments
I was asked a couple of days ago to add a disclaimer to the commenting section on a WordPress Blog, something like: “Commentators are asked to be polite, stay on topic. While we do monitor and moderate comments, they are …
Test and Fix if your Browser can be exploited by Poodle
 Most browsers are vulnerable, there were plans a remove SSL3 anyway. Here’s a simple test and supplied fixes for most browser types on most platforms.
Most browsers are vulnerable, there were plans a remove SSL3 anyway. Here’s a simple test and supplied fixes for most browser types on most platforms.
General details on the Poodle SSL3 vulnerability here.
A fix for Poodle SSL3 Microsoft …
Poodle Vulnerability and Microsoft iis Servers and Shell Shock
People are still busy going through previous projects and installations the growing number of threats offered by the Shell Shock vulnerability, with the list of exploits are constantly growing here.
Well I didn’t quite drop everything, but within 24 …
Fake domain name sales
I was so happy with the response I got with my post regarding the fake ICANN appraiser scam a couple of months ago, I thought it worth sharing each of the dodgy domain name practices I come across as they …
inexcusable that there was only a password protecting this much sensitive data
JPMorgan Password Leads Hackers to 76 Million Households
Inexcusable that there was only a password protecting this much sensitive data.
2FA, Smart Card… we have so many tools available now, there really is no excuse for such …